Quantum computing represents one of the most exciting technological advancements of our time, promising to…
Proactive vs reactive cybersecurity: Why you need to know the difference
From online banking, shopping and social media to video calls with grandchildren, the internet is an integral part of our daily lives. Our homes are becoming smarter with Internet of Things (IoT) devices like thermostats, speakers, security cameras, fridges and vacuum cleaners, combined with our hand held and wearable devices, we’re constantly online. This makes understanding proactive & reactive cybersecurity increasingly important.
However, every convenient connection is a potential access point for a cyber crook.
Cybersecurity knowledge and protection is no longer only for big corporations or government agencies, it’s something we all need to think about. The Australian Cyber Security Centre (ACSC) cybercrime reports increased from 76,000 in 2022 to 94,000 in 2023 – that’s almost a 24% jump in just one year.
Regardless of your age and whether you spend hours a day online or only occasionally, everyone is a target for hackers and scammers.
How cybercriminals exploit your digital footprint
The personal information stored in your online accounts is a valuable asset that cybercriminals can use or sell on the dark web. Once they have your information, it’s used for things like stealing from your financial accounts, extortion or spending with your credit card.
With online banking and shopping, your financial information is also a click away on fake websites that look remarkably like your bank or favourite online store. These impostor sites trick people into entering login details and credit card information.
Those family photos you share, sent emails, websites visited – all of this is part of your private life and is specific information to create what’s called a data profile. With enough data profile information, cyber crooks can easily pretend to be you online.
Cyber protection or security is all the steps we take to keep our online information and activities safe from “bad actors” – people who want to steal and misappropriate your identity for financial gain.
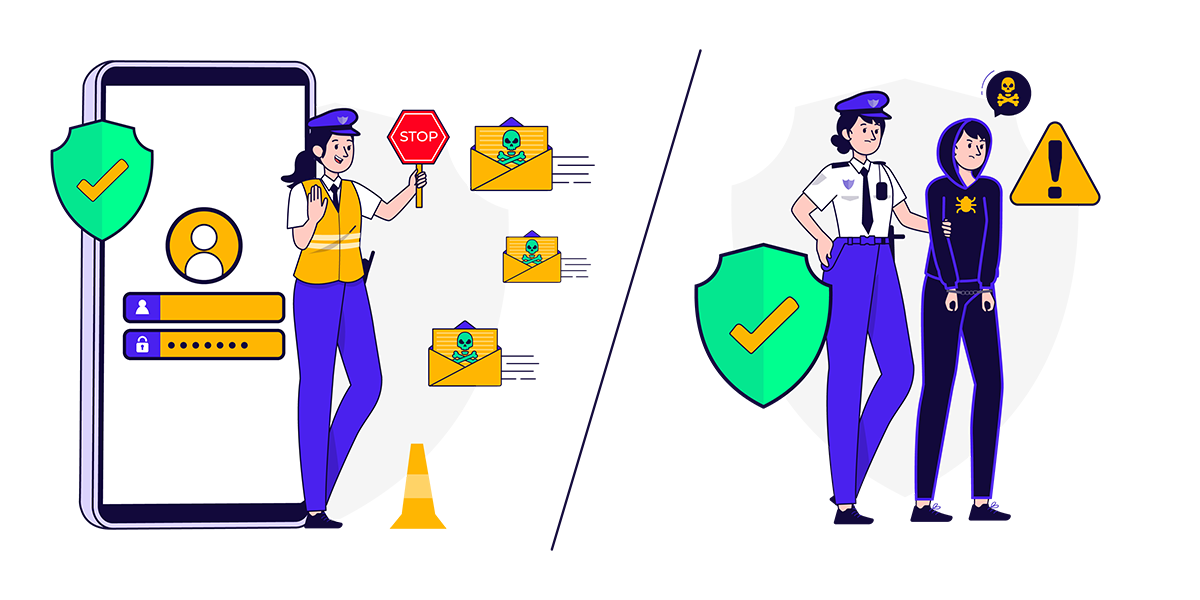
Reactive cyber protection: Yesterday’s approach
Your home ideally has ample smoke detectors throughout and fire extinguishers to prevent a small fire from becoming a major disaster. The internet is like living in a bushfire-prone area. Threats are always present, and conditions can change rapidly. Especially today, where the dark web enables cybercrime to flourish, and AI advances mean anyone with some basic skills can launch highly convincing attacks at speed and scale.
Reactive cyber protection is the typical tools people and businesses have used to manage cyber attacks until now. Reactive cyber tools take action after something bad has happened. Reactive cyber protection includes tools like antivirus software and firewalls. These work by:
- Defending against a maintained list of known threats (like a “most wanted” list)
- Scanning your computer or network for matches on this list
- Blocking or removing anything that matches
Reactive measures also look like changing your password after your account has been compromised and updating software only when you notice your device is playing up.
With reactive measures, you’re always steps behind today’s cybercriminals, as it doesn’t protect against modern attacks. The damage is already done by the time a cyber security program or person responds.
Why preemptive cyber protection is a must have today
Antivirus and firewall can remove a threat and stop it from happening again, but wouldn’t it be better if it couldn’t get through in the first place?
Instead of cleaning up after something has infiltrated, proactive cyber protection actively works to detect problems so it can prevent them. It blocks and removes malicious attempts from the most wanted list, while also applying advanced algorithm technology to identify unusual activity and fake websites.
Proactive protection also works continuously, not just when you remember to run a scan. Many solutions are quick and simple to install, and work quietly in the background, only alerting you when it detects a potential issue.
Other proactive ways to protect your data:
- Create complex passwords for each of your accounts. Password manager’s are great for generating and securely storing unique passwords.
- Enable 2-Factor Authentication
- Regularly update your operating system, apps, and browsers
- Change your router’s default password and enable its built-in firewall
- Stay informed about the latest cyber threats and scams.
Making advanced cybersecurity simple
By taking proactive measures to guard your information and prevent yourself from falling for scams, you can go about your activities without worrying about someone getting into your device or accidentally putting your credit card information into a phoney site.