Today's reality is we have the entire world in the palm of our hand and…
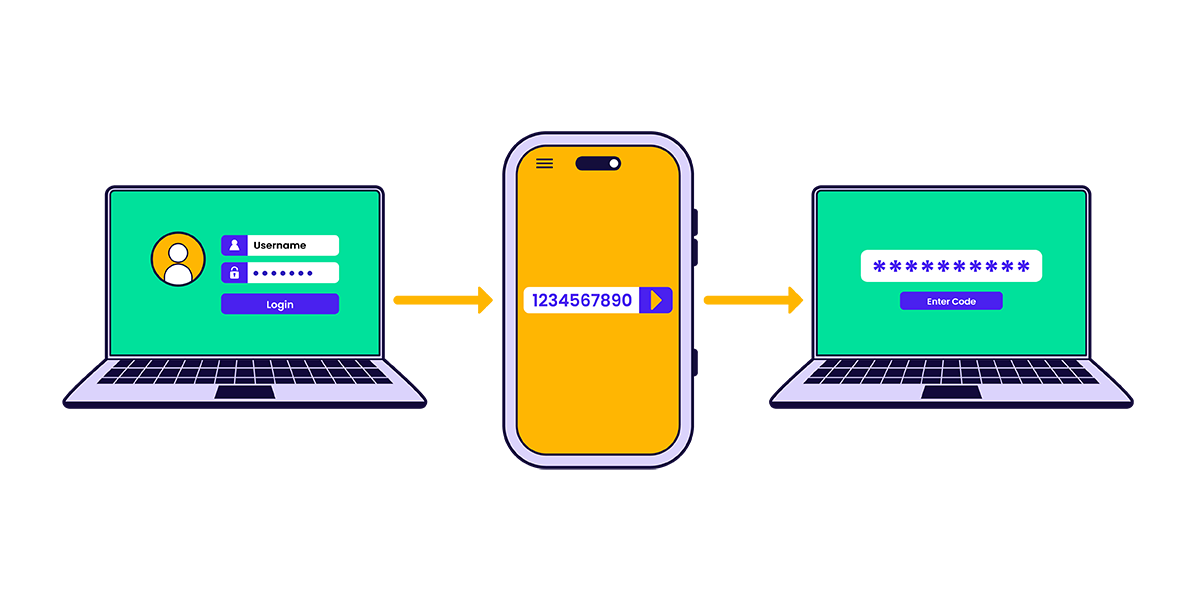
Two Factor Authentication for beginners
Our passwords are one thing that keeps digital predators out of our online accounts. However, in today’s world of cyber attacks and hacking scams, even a regularly changed password isn’t enough to keep our accounts secure (although it’s still important to do this).
A password is like a front door key. Anyone with a key can gain access. Two-Factor Authentication is the separate deadbolt a locksmith changes daily! Imposters can’t access your accounts without the additional verification step enabled 2FA requires. Multi-factor authentication or 2-step verification are other terms for 2FA, but for simplicity and this blog, we’ll stick with 2FA.
Why use 2FA?
With the increasing prevalence of hacking through phishing and malware scams, and company data breaches, Two-Factor Authentication (2FA) has become a necessary security addition to protect our personal data.
Remember the massive data breaches with Optus, Woolworths and Medicare? Millions of customer emails and passwords were exposed, leaving countless accounts vulnerable, as credentials can be sold and swapped in online marketplaces and hacking forums. A regular password grants immediate access to an account, but with 2FA enabled, anyone who got hold of those login details can’t get in without that extra piece of information.
Why this matters to you
- Without 2FA, hackers who obtain your login credentials could access your bank accounts, credit cards, or payment platforms, potentially draining your funds or making unauthorised purchases.
- Cybercriminals could use your personal information to open new accounts, apply for loans, or commit crimes in your name, leading to long-term financial and legal consequences.
- Unauthorised access to your email or social media accounts could expose private conversations, personal photos, and sensitive information, which is great material for blackmail or reputational damage.
- Hackers could delete or encrypt your valuable data, including important documents, irreplaceable photos, or work-related files.
- Cyber criminals could lock you out of your own accounts by changing passwords and recovery information which is difficult to and potential loss of digital assets.
- Spread of attacks: Compromised accounts could be used to send phishing emails or malware to your contacts, potentially harming your personal and professional relationships.
- Legal liability: If your compromised accounts are used for illegal activities, you might face questioning or legal consequences, even if you’re not directly responsible.
How does 2FA work?
2FA methods are super user-friendly. Setting them up usually takes a few minutes, and using them is a quick extra step during login.
Authenticator apps are the most secure method when you set them up to specific accounts (bank, social media, email, user platforms). The app generates unique codes every few minutes that can only be used for that account. After entering your password, the system will prompt you for the authenticator code.
- Download a trusted authenticator app from your phone’s app store
- Go to your account’s security settings and find the 2FA option
- Scan the QR code or enter the secret key shown to connect your app
- Enter the code from your app to confirm it’s working
- If offered, securely store backup codes in case you lose your phone.
For text or email verification:
- In your account’s security settings, choose to receive verification codes by text or email.
- You might get a test code to make sure it works
- From then on, you’ll need a code every time you log in.
Biometric 2FA uses your unique fingerprint or face to unlock your accounts. iPhone and MacBook most commonly have this — not all devices support biometric authentication. While it is super convenient, inputting your biometric data into a site or platform has some security concerns.
Security keys are small are another 2FA mechanism using, physical devices that plug into a device to confirm your identity when logging in. While less common, they still offer this essential added layer of security we all need.
Is 2FA convenient? What if I lose my phone?
Setting up 2FA takes just a few minutes. After that, it’s one extra step during login — a small price to pay for significantly increased security.
With losing your phone, notify your carrier to deactivate your SIM card (and get a new one) to prevent unauthorised use. Enact alternative login or account recovery methods (answering security questions or receiving a temporary code via email) and change your passwords asap.
Some services allow you to register a backup phone number or email address for receiving verification codes and account recovery methods if you lose your primary device.
Digital Security requires a Multi-Layered approach
Two-Factor Authentication is a fantastic way to help prevent unauthorised account access. However, online threats come at us from all angles — from email phishing scams to malware-laden websites. For ultimate online security, install the Sapher browser extension. It offers real-time threat analysis to anticipate cyber threats before they can infiltrate your device.
Take control of your online security. Enable 2FA today, and explore how Sapher can be an additional trusted partner in securing your digital life.


